[ad_1]
Three years after one of the most visible hacks in recent history played out in real-time in front of millions of Twitter users, one of the hackers responsible for the breach will now serve time in federal prison.
Joseph James O’Connor, 24, was sentenced Friday in a New York federal court to five years in prison after pleading guilty in May to four counts of computer hacking, wire fraud and cyberstalking. O’Connor also agreed to forfeit at least $794,000 to the victims of his crimes.
O’Connor, a U.K. citizen, was extradited from Spain at the request of U.S. prosecutors earlier this year and has remained in custody since.
In the hearing, Judge Jed S. Rakoff said O’Connor will likely serve about half of his sentence after spending more than two years in pre-trial custody.
O’Connor faced a maximum of 77 years in prison, according to Reuters. Justice Department prosecutors called for O’Connor to serve at least seven years in prison.
In court, O’Connor said his crimes were “stupid and pointless,” apologized to his victims, and asked the judge for leniency.
According to prosecutors, O’Connor “used his sophisticated technological abilities for malicious purposes — conducting a complex SIM swap attack to steal large amounts of cryptocurrency, hacking Twitter, conducting computer intrusions to take over social media accounts, and even cyberstalking two victims, including a minor victim.”
The government said O’Connor, known by his online handle PlugWalkJoe, was part of a group that broke into dozens of high-profile Twitter accounts, including Apple, Binance, Bill Gates, Joe Biden and Elon Musk to spread cryptocurrency get-rich-quick scams in July 2020.
O’Connor used phone-based social engineering techniques to trick Twitter employees into granting the group of hackers access to Twitter’s network. One of the other hackers convicted of the Twitter breach, Graham Ivan Clark, also known as Kirk, used the access to Twitter’s network to abuse an internal admin tool to hijack and reassign Twitter user accounts.
A screenshot of the Twitter admin panel that the hackers breached in order to reassign access to Twitter user accounts. Image Credits: TechCrunch (supplied)
Twitter temporarily blocked users from posting to the site as it grappled with the intrusion, as millions of users watched in real-time as their timelines flooded with cryptocurrency scams from some of the most recognizable names on the planet.
A subsequent investigation by New York’s state government, which accused Twitter of inadequate cybersecurity protections, found that the hackers broke in by “calling Twitter employees and claiming to be from Twitter’s IT department,” then hijacked the Twitter accounts of politicians, celebrities, and entrepreneurs to tweet “double your bitcoin” scams.
The scam netted about $120,000, according to public blockchain records.
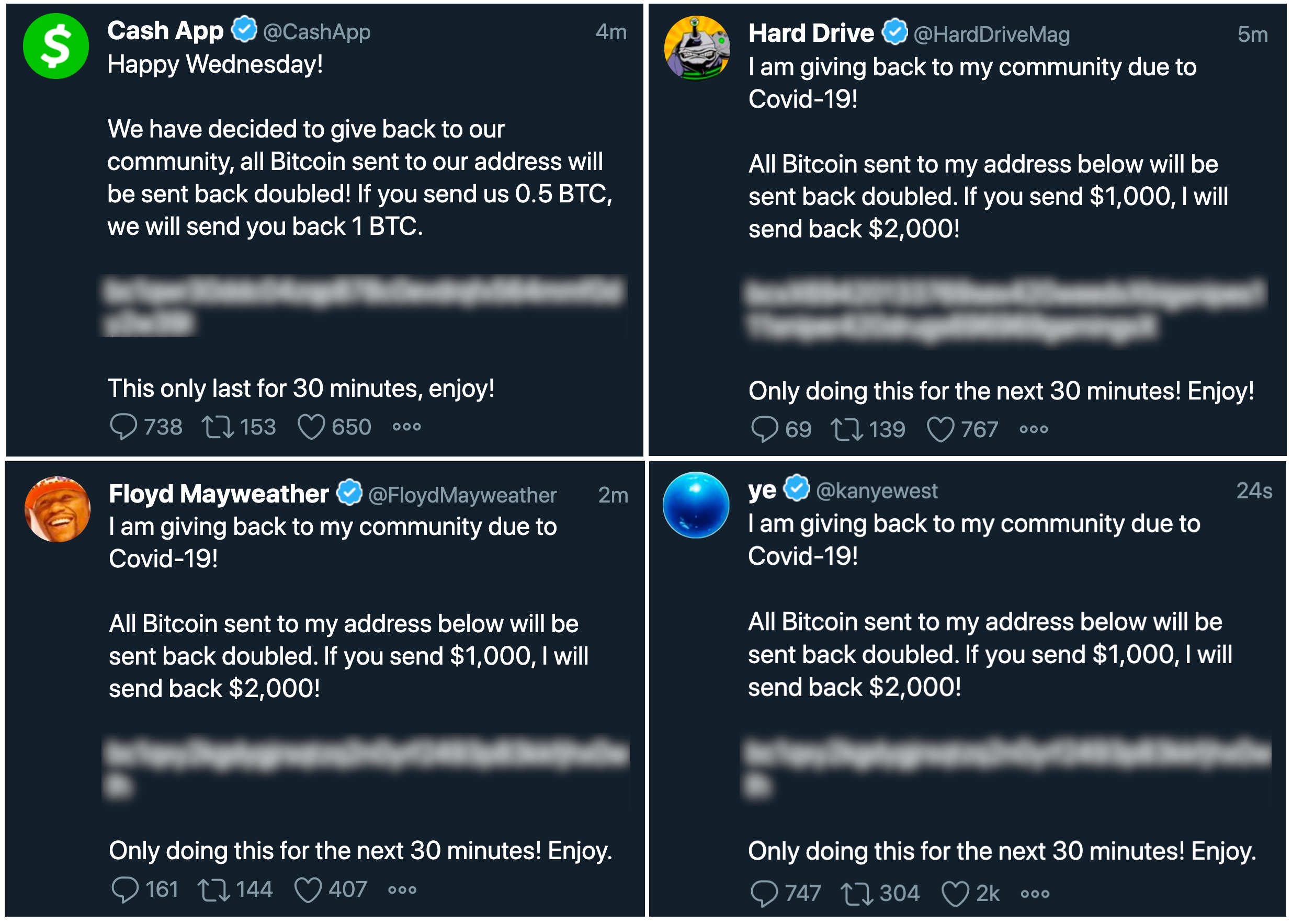
Several of the tweets that were published during the 2020 Twitter hack. Image Credits: TechCrunch
The breach prompted Twitter to improve its cybersecurity controls, introducing hardware security keys for its employees to prevent future phishing attempts.
Two years on from the hack, more explosive allegations about the breach came to light.
Peiter “Mudge” Zatko, who was hired as Twitter’s head of security months after the breach, later described the hacker’s access as achieving “god mode,” which allowed them to imposter-tweet from any account they wanted. Zatko called the incident “the largest hack of a social media platform in history” in a whistleblower complaint filed with federal regulators in 2022, in which Zatko accused his former employer of cybersecurity failings.
Twitter auto-replied with a poop emoji in response to an emailed request for comment, as it has done since a short time after Elon Musk acquired the company.
[ad_2]
Source link
